\begin quote
Steve Mann (Canada) is the recipient of the 2004 Leonardo Award for Excellence. In his winning article, the author presents "Existential Technology" as a new category of in(ter)ventions and as a new theoretical framework for understanding privacy and identity. Mann has written more than 200 research publications and has been the keynote speaker at numerous industry symposia and conferences. His work has been shown in museums around the world, including the Smithsonian Institute, the Museum of Modern Art in New York, the Stedelijk Museum in Amsterdam, the Triennale di Milano and the San Francisco Art Institute. He received a Ph.D. from MIT in 1997 and is now a faculty member at the University of Toronto. Read his Leonardo article.
--Leonardo ed.
Local cache of PDF file of the article entitled "Existential Technology"
Policy and procedure become part of a globally networked computational infrastructure. Even simple fixtures such as lighting, heating, toilets, and handwash faucets, become part of a globally connected network, with programmed policy and procedure. The control-systems theory of micropunishment and micromanagement (cite procieee) means that the building owner, and not the user, dictates, for example, how long the sensor operated handwash faucet will run before it annoyingly shuts off.
author = "Steve Mann",
title = "Humanistic Intelligence/Humanistic Computing:
`WearComp' as a new framework for
intelligent signal processing",
journal = "Proceedings of the IEEE",
volume = 86,
number =11,
pages = "2123--2151+cover",
month = "Nov",
year = "1998"
URL = "http://wearcam.org/procieee.htm"
But writing a letter to the building owner will often have little or no
effect, other than a referral to head office, or maybe a vague reference
to the Federal Energy Management Program. And when something goes wrong,
it is difficult to determine who is responsible.
In addition to controlling the fixtures within a building, buildings often have sophisticated access control to make sure that individuals entering the establishment are properly processed.
At the same time, the officials operating these establishments may often escape a means of being similarly held accountable for their actions, if by nothing more than the uncertainty of who, in particular, is responsible for particular actions.
Moreover, building owners have developed means and apparatus for containment, confinement, and other forms of processing they wish to apply to individuals passing through their establishments.
For example, U.S. Patent number 4341165 describes a revolving door which allows the building owner to entrap and detain persons it might wish to detain. U.S. Patent number 4586441 describes a similar invention that also analyzes the individual so entrapped. U.S. Patent number 4461221 describes a system for detaining robbers on premises. U.S. Patent number 4341165 also describes a similar system. U.S. Patent number 5311166 describes a system for directing water and chemical weapons on undesirable persons entering a premises. U.S. Patent number 5528220 describes a device that automatically sprays chemical weapons on individuals entering an area where the owners of the establishment would prefer that individuals not enter.
In addition to access control, there are also perimeter security devices such as that disclosed in U.S. Patent number 5182764 to scan individuals for weapons, and other forms of devices that allow officials or security guards to see through clothing to inspect individuals. Some systems allow officials to secretly search individuals without their knowledge or consent, and without any kind of due process.
U.S. Patent number 4796311 describes an intake facility whereby individuals may be required to undress completely, while being viewed by facility owners or the like, who can also monitor and control a decontamination process. U.S. Patent number 4858256 and U.S. Patent number 5551102 describe similar ``decon'' systems, whereby an individual may be prevented from passing from one section to another unless the individual complies with orders or requirements of those in control.
Julia Scher provides a critical framework in which to understand such concepts as what she calls:
Historically, quarantine, delousing, and showers with airtight and watertight locking doors that cannot be opened by the occupants have been used to subject detainees to various chemical substances. Business models, and methods of processing individuals passing through official spaces, customs, borders, quarantine, airports, train stations, buildings, offices, prisons, and the like, are well known throughout history, and continue to be developed. (Consider, for example, modern airports that are equipped with mass decontamination facilities for processing up to 700 suspected disease carriers per hour, as described in http://wearcam.org/envirotech/decon_summary.htm.)
However, the art of protecting the individual person, personhood, and personal space, is somewhat lacking. Although physical protection of the body through armour is a centuries--old tradition, dating back to the days when five to seven layers of rhinoceros skin were used to protect the body during battle, such physical protection of the body has not kept pace with informatic developments in protection of property as we evolve from a physical world to an informatic world.
Although protection of property has evolved from medieval fortresses toward bank towers with glass doors protected by card readers and retinal scanners, the protection of the body has not kept pace with the move from physical stone fortresses to more the informatic protection of buildings.
Similarly, the emphasis of protection of the establishment has shifted from protection of physical property such as land, buildings, and resources, toward protection of intellectual ``property''. Globalization is largely driven by computer networks, and likewise, the protection of intellectual ``property'' has emerged as a situation of growing complexity. Take for example, the ``purchase'' of a typical computer or computer program. What we now often have is a change from what might have once been a purchase, into a license. The complexity of this whole paradigm shift was addressed in a recent traveling art installation entitled ``SeatSale: Seating made Simple'' (http://wearcam.org/seatsale/index.htm), in which a simple object like a chair, was connected to a global computer network with a license manager. Rather than owning the chair, you license the use of the chair. Sliding a credit card through a slot in the chair causes 23 seat spikes to retract, for the duration of a ``Seating License (TM)''. (See Fig.:seatsale.)

The point of SeatSale was to show how the protection of ``Intellectual Property'' violates something else. That something else is called ``Humanistic Property'' cite firstmonday.
author = "Steve Mann", title = "Computer Architectures for Protection of Personal Informatic Property", journal = "First Monday", volume = 5, number = 7, month = "July", note = "http://firstmonday.org/issues/issue5_7/mann/index.html", year = "2000"
Shortly after SeatSale, I created a performance piece called ``Ouijagree''. On Fri Jan 5 18:12:34 EST 2001, I plugged in a new computer for the first time. Like many new computers, it had been ``tagged'' with unsolicited advertising including a sticker reading ``Designed for Microsoft Windows 2000''. I wondered how this corporate tag was any different than graffiti that kids use to tag their gang's territory. The computer also seemed to have been tagged internally with some unsolicited advertising as well, because a software message popped up on the screen indicating Terms and Conditions, which I certainly did not agree with. (I had not asked for any software for this computer since I ordinarily use only FreeSource such as GNU Linux). Among other things, the Terms and Conditions forbid the practice of science (e.g. trying to understand how a program works, its underlying operational principles, etc.). So, having three of the students working with me on the computer, the four of us placed our hands gently on the mouse, to position the cursor wherever it was summoned to go.
Ouijagree contained elements of ``Oui'' (French for ``yes'', as in ``yes, we agree''), and the Ouija board's planchette. The mouse served the role of planchette. On the abstract level, we might say that the spirits of the dead are bound by the Terms and Conditions of the contract, whereas on the more concrete level, since no one particular one of us moved the mouse, it would be difficult to discern which of us, if any, were to be bound by these unfair and outrageous Terms and Conditions.
The Ouijagree performance was a very simple example of what I call Existential Technology (technology of self determination and mastery over our own destiny). Ironically, our mastery over our own destiny (e.g. our freedom) came from our very lack of control over the situation (e.g. the fact that no one person exercised decisive voluntary control over the position of the planchette mouse).
In this paper, I will describe what I believe to be much more profound and powerful examples than that provided by the Ouijagree performance. In particular, what I will describe is a concept I call ``being bound to freedom'', and various ways in which the individual can wear or carry an apparatus of self-demotion (corporatization). By becoming one with the corporatized ideal of diffuse indirection, we can, in effect, tame the monster of globalization and corporatization with a piece of itself.
Figure:clerks illustrates this imbalance by way of an individual interacting with a clerk who either is, or pretends to be, under the control of a manager who either is, or pretends to be under the control of a chief technology officer, who either is, or pretends to be, under the control of a board of directors, etc..:
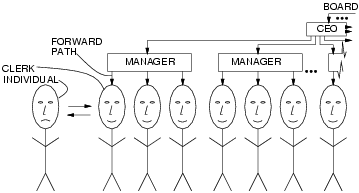
A typical example of such a situation is when an individual attempts to negotiate with a used car salesman, and the used car salesman might say something like ``I'd love to give you the car for two thousand dollars; let me check with my manager''. The used car salesman then disappears into a back room, alone, and has a coffee, and reads a newspaper for a few minutes, and then comes out and says ``I'd love to give you the car for two thousand dollars but my manager won't let me.''. Although the salesman never talked to a manager, the salesman has some degree of power over the customer by virtue of being able to credibly pretend that he is bound by a higher and unquestionable authority. A credible, articulable, higher and unquestionable authority allows representatives of organizations to obtain external blame and excuses for what would otherwise be irrational or disagreeable actions.
Unfortunately the individual person does not ordinarily enjoy the same luxury as the clerk, and must therefore behave more rationally, or risk seeming irrational, rude, or otherwise inappropriate.
Another example is that of video surveillance. If we visited a friend's house where video surveillance was used because that person did not trust us, we would likely be quite angry. However, we often accept the use of video surveillance systems by owners of large organizations, simply because it is not clear who is responsible for the installation of such systems. In my ShootingBack performance ( http://wearcam.org/shootingback.html) I explored this phenomenon, by asking clerks at department stores, and the like, why they had placed me under video surveillance. Their typical response externalized the responsibility to some higher and unquestionable authority such as management. When I attempted to follow the chain of responsibility upwards, management indicated the directive was from head office, and head office argued video surveillance was just policy, or for insurance purposes, or the like. Thus there was no clear accountability for the situation.
If an individual carried a handheld video camera around videotaping clerks, casino operators, police officers, customs officials, and the like, the individual might be regarded as strange, rude, or otherwise acting in an inappropriate manner.
The individual could rely on religion, as a manager, by, for example, wearing a camera contraption as part of a religious order. Just as religion allows individuals the right to wear special headwear even as uniformed employees (e.g. to wrap their heads in various materials that would otherwise be regarded as inappropriate), a new religion such as the ``personal safety religion'' could be invented, that required its members to wear cameras.
Thus religion could form a similar purpose to the manager for the individual, but there is the danger that others (including clerks) may dismiss the individual as a religious freak. Therefore, what I invented was another way for the individual to have excuses for, and to externalize blame for, otherwise irrational or disagreeable actions.
An important aspect of my invention is for the individual to be able to nonconfrontationally inflict fear of accountability, uncertainty, or doubt on persons exerting physical or other coercive force, or the threat or possibility thereof, upon the user of the invention. I did this by way of an incidentalist imaging possibility.
Incidentalist imaging refers to imaging which can be made to seem as if it occurs merely by chance or without intention or calculation. An incidentalist imaging system may in fact blatantly capture images (as by an articulable requirement from a higher authority to do so), or it may present itself as a device that could capture images in a way in which it is difficult to discern the intentionality of the use of the invention.
Figure:selfdemotion illustrates the situation of a wearable computer user who is able to either be, or pretend to be, under the control of a Safety Management Organization (SMO).
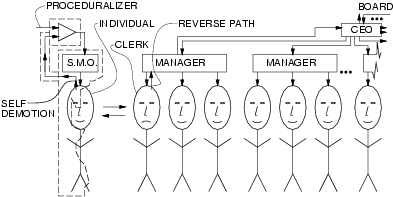
Ordinarily there would be no such back channel, or the back channel would be reduced, or its existence may even be denied or obscurred by the CLERK. For example, if an INDIVIDUAL complains about video surveillance systems in use by a CLERK, then the CLERK will simply refer the INDIVIDUAL to management, and management will be likely only available on certain limited hours, and after waiting extensively and being held up and delayed in line extensively. Then management will likely say the directive for use of surveillance comes from head office, and refer the INDIVIDUAL to a head office, where the INDIVIDUAL will spend several hours waiting on hold and calling various telephone numbers, etc.. The head office will then often say that the surveillance is used because the insurance company requires it.
However, if the INDIVIDUAL takes out his or her own personal handheld camera and photographs the CLERK, indicating that the SMO requires it, a very fast back channel (REVERSE PATH) will arise. Quite often the MANAGER will immediately become available, and the INDIVIDUAL will no longer have to wait in line or come back on a certain special day to talk to the manager. The CLERK will, in fact, desperately seek a manager to avoid being photographed. The matter will therefore rapidly escalate to the highest available level of authority.
This system has a symmetrizing effect in which the individual and manager either snap out of their respective roles, or a back channel is forced, disrupting the normally one--way nature of the control flow from the top--down of management to the CLERK. Thus the individual human becoming a clerk forces the clerk to become an individual human and make responsible decisions outside the scope of just being a clerk.
In addition to an SMO, the INDIVIDUAL can also choose to be bound by (or to pretend to be bound by) an SMO that is itself bound by a higher authority such as an insurance company. Thus, in one embodiment, the INDIVIDUAL could, for example, take out a life insurance policy that required him to wear a personal safety device that recorded video at all times.
Thus an individual wishing to wear a video capture and recording system merely signs up with a life insurance company (e.g. EXISTech Corporation) that requires him to do so. A small premium of one cent per year is paid by the individual primarily for the reason of being bound by the requirement to wear the device. The life insurance company provides the individual with a choice of two programs, one being one cent a year wearing a camera, and the other being two cents a year not wearing the camera. Thus the individual wishing to wear a camera system simply selects the lower premium, and then blames his apparently irrational actions (like constantly wearing a camera system) on the insurance company. EXISTech Corporation simply becomes the individual's corporationality (corporate rationality).
Thus the life insurance company provides the individual with a means for articulably externalizing his own irrational actions. Now the individual can say ``I'm wearing this camera because my manager (SMO) requires it, and the insurance company requires the SMO to require me to wear it, etc.. This reverse chain of command is denoted by amplifier 104B.
Preferably, in the experimental apparatus, a PROCEDURALIZER is used to allow the individual to follow, or to appear to follow, a prescribed procedure without appearing to be thinking for himself or herself. The lack of apparent individual thought or intentionality, allows the individual to become or seem to become a clerk, which is what forces the CLERK to be human in being forced to think and make decisions for himself or herself.
Moreover, a secret input (SELF DEMOTION) to the amplifier may actually originate by the INDIVIDUAL. In this sense, the INDIVIDUAL is actually bound by his own wishes. Thus the SMO may actually be directed by the INDIVIDUAL to bind the INDIVIDUAL to certain terms and conditions.
My Manager also evolved to other pieces to explore the freedom associated with covering, restraining, and diminishing of the capabilities of the human body, using such works as ``PleaseWait'' (http://wearcam.org/pleasewait.htm) which prevented me from seeing or hearing anything until a person identified themselves by sliding an ID card through a slot on my head (See Fig.pleasewait and Fig.colorplate)
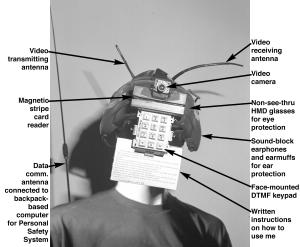

PleaseWait bears some similarity to Kac's Telepresence Garment (cite kacwearable):
Instead of adorning or expanding the body, however, the Telepresence Garment... foregrounds the other meanings of the verb ``to wear'': To damage, diminish, erode, or consume by long or hard use; To fatigue, weary, or exhaust.
author = "Eduardo Kac",
title = "DIALOGICAL TELEPRESENCE ART AND NET ECOLOGY",
editor = "Goldberg, Ken",
booktitle = "The Robot in the Garden: Telerobotics and Telepistemology in
the Age of the Internet",
pages = "180--196",
publisher = "MIT Press",
address = "Cambridge, Massachusetts",
year = 2000,
URL = "http://www.ekac.org/dialtelep.html",


Web-based audiovisual capture and immediate playback made subjects very aware of the recording, capture, and playback capabilities of the system. In many ways, Sicherheitsglaeser was the audiovisual equivalent of the Maubrey's audio wearable apparatus (cite maubrey) described in http://home.snafu.de/maubrey/ as listed in www site http://online.sfsu.edu/~infoarts/links/wilson.artlinks2.html of http://userwww.sfsu.edu/~swilson/
author = "Benoit Maubrey", title = "Audio Jackets and Other Electroacoustic Clothes", journal = "Leonardo", year = 1995, volume = 28, number = 2, month = "April/May", URL="http://www-mitpress.mit.edu/e-journals/Leonardo/isast/journal/toc282.html"
For shooting my documentary video with my EyeTap system (e.g. eyeglasses that cause the eye itself to function as if it were a camera (cite{procieee)). My wearable apparatus is controlled by a handpiece that looks (and works) alot like a musical instrument. This ``keyer (cite{keyersabout)''
http://wearcam.org/septambic/ http://about.eyetap.org/library/weekly/aa120400a.shtmlhas various keys that can be pressed in various combinations to form various chords. I unplugged my keyer so that I would have no control over my EyeTap rig, but before I unplugged my keyer, I asked my wife to MAYBE press C before unplugging the keyer, so that I would not know whether or not my eyeglasses were remembering (or recording or transmitting) anything. The keyer, like a musical instrument that I usually start off by playing in the key of G (Grab), then change to the key of C (Capture), was no removed so that I had no way of controlling the function of the apparatus. Prior to the removal, I had my back turned away so I could not see what she was keying, so that I would not know whether or not I was in the key of C.
Finally, I switched to the key of lost: I locked my waistworn computer rig shut with a small padlock I didn't have a key for. (I gave the key to my manager so I would not have it.) Thus I could not access any of the controls or get at the system or determine whether or not the system was in Capture mode.
Now once I was MAYBE playing in the key of C, but definitely playing in the key of lost, I wandered into the Casino, with the film crew to follow.
The film crew managed to sneak in all their film gear (this was not merely video, but, rather a film crew with a large Arriflex motion picture camera that shoots real celluloid film). The line producer (Alexi Steele) distracted the guard, while the cameraman (Rudy) pretended to be close friends with his assistant, giving her a big hug, with the camera hidden between them, as they walked in past the guards. The sound crew also managed to sneak in past the guards, and so as I walked in, the crew quickly assembled inside, and followed me up the escalator. There is a tall escalator going up a very grand entrance, and the crew knew that they could not be attacked in the confined space of the escalator, so even after detection, the assailants would need to wait until the crew got to the top.
The assailants were waiting at the top.
The film crew explained that they were making a documentary
of me (that they had been following me around, in my day-to-day life,
etc.,) but the crew was asked to not take pictures,
so I continued to wander around and make my own documentary, without the film
crew able to follow me. Nobody seemed to know that I
Later, I left and met up with the film crew who were waiting outside and had been prohibited from shooting inside the casino.
Casinos have traditionally been associated with money laundering and crime, so that shooting investigative video within casinos raises some interesting questions as to what is prohibited and what is allowed (e.g. the question as to whether photography is often prohibited in order to hide evidence of wrongdoing). Artists are beginning to ask questions about rules and regulations, and even crime, and what is crime, for example, as articulated by Stephen Wilson:
Deconstructing Crime: What's a crime? Who defines it? What are our prejudices about crime? Are street crimes worthy of more attention than other crimes against the community such as poisoning the Bay or creation of dangerous products that kill or maim?http://userwww.sfsu.edu/~netart/crimezy/crimemain.html (See also http://www.ctheory.com/article/a067.html)

Some 15 years later, this trend still continues, with my having been asked to do a fashion show as the grand finale of the Technology Entertainment and Design (TEDCity) conference, in June 2000. This show encapsulated and summarized fifteen years of cyberfashion, including such pieces as the early wearable photographic apparatus, and the more recent ``Maybe Cameras'' of 1996. (See Fig.:fashionshow)


I narrated the presentation of the TieDome at the fashion show as follows:
The tiedome: a necktie with an attitude. Wear this to your favorite gambling casino, department store, or anywhere else where photography is prohibited.
TieDome was one of many pieces I constructed to match the decor of just
about any gambling casino or department store. The irony here is that
these pieces
Since image capture was involuntarily controlled by the wearer (e.g. heart rate being an externality not directly under her intentioned control), the apparatus provided an incidentalist element. Moreover, if an assailant objected to the camera, or the possibility of a camera, by assailing the wearer, whether verbally or otherwise, the frame rate would increase.
Thus a potential perpetrator who became upset at the wearer for photographing him, would cause her heart to beat faster which would cause her to take more pictures of him.
Since this feedback loop was beyond her control, it could be said that the assailant was taking pictures of himself by agitating her. (See Fig.:heartcam)



You see, even though I built it, I cannot open it, because I have replaced the thumb operated latches with fingerprint scanners. A computer inside the case matches the fingerprints against a database, and I have simply put myself in the /etc/deny directory.
The Griefcase bears the written instructions on its exteriour surface:
This briefcase is property of EXISTech Corp. By extension, it is thus considered to be part of EXISTech's Corporate headquarters. Therefore, it requires the same degree of protection as EXISTech's Corporate Headquarters, namely that it be protected from undocumented access to its contents, or to access by strangers.Accordingly, an audit trail log, with fingerprints of anyone and everyone opening this briefcase, whether for Business, or simply for routine inspection, must be maintained.
Routine inspection may include inspection by officials, such as law enforcement personnel, customs officials, etc., as well as by private security officers such as those stationed at the egress of establishments such as department stores, public libraries, and other places where bags and personal belongings are checked upon exiting or entering these establishments.
In order to ensure this accountability, the owner or person carrying this briefcase cannot open it. Only persons other than the owner of this briefcase can open it.
Anyone opening this briefcase, whether they be law enforcement officers, customs officials, military police, or private security forces, must therefore be fingerprinted, and the fingerprints must be maintained in a time-stamped accountability archive. Additionally, this briefcase contains a video surveillance system to document any inspection of its contents, in order to ensure that the contents are not compromised by strangers or corruption.
Compliance with these directives is enforced by both policy as well as by using the latest in keyless lock security technology. The briefcase uses keyless thumb latches activated by pressing both thumbs on the latches simultaneously. The onboard microprocessor scans the thumb prints of the person attempting to open the briefcase. If the fingerprints are those of the owner, the briefcase is not opened. If the fingerprints are those of any person other than the owner, the fingerprints are transmitted by way of a built in cellular telephone data communications system, for remote archival and comparison with a database of known criminals. Assuming no criminal match is found, the briefcase can be opened by anyone other than its owner, pending successful transmission and archival of that person's fingerprints to a logfile mirrored across EXISTech's global network of servers.
As Assistant Mailroom Clerk for EXISTech Corporation, my job is simply to deliver the mail, and I, of course, cannot be trusted with access to the mail. Therefore, I cannot open the Griefcase.
This situation creates something I call Submissivity Reciprocity. That means that anyone wishing me to submit to a search of the case, must submit to being fingerprinted.
Additionally, by handcuffing one of my hands to the case, and leaving the key in EXISTech's level 4 laboratory (or inside the briefcase itself), I am unable to even try to open the case, because I then cannot get both thumbs onto the scanners at the same time. Thus I require the help of the person wishing the case to be opened.
A smaller wallet size version of a similar apparatus is described in http://wearcam.org/griefcase/idwallet.htm.
surveillance has developed into an intangible network(s) whose technology has reached such a level of effectiveness and persuasiveness that there is no sure way of knowing when we are actually being watched. If we assume that we are being observed at all times, there is no need for an overly oppressive, coercive mechanism of control; surveillance becomes self-regulating and control is internalized.
This point of view is also similar to the ``carcereal state'' and the framework described by Michel Foucault in Surveiller et Punir. This work is related to the Situationist movement, as she writes:
By tinkering with the tools and vocabularies of different controlenvironments (especially technological)-through admixture and recontextualizations, i.e. purposeful dislocation--it is possible to subvert thedeceptively friendly relationship we've come to expect from our tools of controland surveillance. I have been displacing the organs of control by actuallytaking the tools and language of surveillance and fashioning them into assemblages. In other words, I make art from the tools of control.(http://www.insecuritybyjulia.com)