ID card holder for RECIPROCAL IDENTIFICATION OF PERSONS
SUCH AS OFFICIALS ASKING FOR IDENTIFICATION
W. Steve G. Mann
A wearable or carryable means and apparatus for the collegial identification
of officials is disclosed.
Identificational reciprocity is built into the apparatus of the invention
so that identification is not inadvertently shown to criminals who might
have stolen a security guard's
uniform or the like, or, in the event that such
criminals may have also stolen a security guard's identification, there is also
provided means of biometric informational acquisition so that
such criminals have a better chance of getting caught.
The invention provides an incidentalist identificational procedure,
so that legitimate officials are not offended by a person using the invention
who would otherwise be perceived as disrespectful
by demanding identification from an official.
FIELD OF RESEARCH
The present research pertains generally to a wearable or carryable
apparatus that provides the user with a means of ensuring that strangers,
especially criminals with a stolen security guard's
uniform, or criminals in positions
of authority, do not obtain information such as ID numbers, credit
card numbers, or the like, from the user of the invention without
also identifying themselves, or undergoing some degree of risk of getting
caught if using fake or stolen identification.
RESEARCH BACKGROUND
Children are often advised by their parents: ``Don't talk to strangers!''.
However, many times individuals may be stopped on the street and asked
for identification by a person who is, for all practical purposes, a
stranger. For example, there is always the possibility
that the trusted uniformed SS man on the street who
demands ``Your papers please!'' may in fact be a criminal, perhaps wearing
a stolen uniform and carrying fake or stolen badges and identification.
In today's society which is teeming with dangerous criminals, buildings
often have sophisticated access control to make sure that everyone entering
the establishment is properly processed, but those wearing uniforms,
such as the officials operating these establishments,
have somehow escaped a means of being similarly identified.
Moreover, building owners have developed means and apparatus for
containment, confinement, and other forms of processing they wish to
apply to individuals passing through their establishments.
U.S. Pat. No. 4341165 describes a revolving door which allows the building owner
to entrap and detain persons it might wish to detain.
U.S. Pat. No. 4586441 describes a similar invention that also analyzes the individual
so entrapped. U.S. Pat. No. 4461221 describes a system for detaining robbers on
premises. U.S. Pat. No. 4341165 also describes a similar system.
U.S. Pat. No. 5311166 describes a system for directing water and chemical weapons
on undesirable persons entering a premises. U.S. Pat. No. 5528220
describes a device that automatically
sprays chemical weapons on individuals entering an area where the owners
of the establishment would prefer that individuals not enter.
Other forms of access control, such as card readers, etc.,
are well known aspects of the prior art.
The field of biometrics is also well established,
through a number of scholarly conferences aimed at producing a utopian
future in which certain select individuals can know the whereabouts of
most other individuals at all times.
In addition to access control, there are also perimeter security
devices such as that disclosed in U.S. Pat. No. 5182764 to scan individuals for
weapons, and other forms of devices that allow officials or security
guards to see through clothing to inspect individuals. Some systems
allow officials to secretly search individuals without their knowledge
or consent, and without any kind of due process.
U.S. Pat. No. 4796311 describes an intake facility whereby individuals may
be required to undress completely, while being
viewed by facility owners or the like, who can also monitor
and control a decontamination process.
U.S. Pat. No. 4858256 and U.S. Pat. No. 5551102 describe similar ``decon'' systems,
whereby an individual may be prevented from passing from one
section to another unless the individual complies with orders or requirements
of those in control.
Historically, showers with airtight+watertight locking
doors that cannot be opened by the occupants have been used to
subject the occupants to various chemical substances.
Such practices and procedures are well known in the prior art.
Moreover, the general concept of ensuring that individuals have their
papers in order, is also a well known aspect of the prior art.
Physical protection of the body through armour is a centuries-old
aspect of the prior-art, dating back to the days when five to seven
layers of rhinoceros skin were used to protect the body during battle.
Such physical protection of the body has not kept pace with new developments
in protection of property. Protection of property has evolved from
medieval fortresses toward bank towers with glass doors protected by card
readers and retinal scanners.
The protection of the body has not kept pace
with the move from physical stone
fortresses to informational protection of buildings.
Little has been done to address the protection of individual Humanistic
Property in a world so obsessed with the protection of Intellectual
Property at the expense of Humanistic Property. In keeping buildings
secure from ``theft'', a new kind of theft has emerged as a side-effect
of the security systems themselves. This theft of Humanistic Property
is addressed in a short article entitled Theory of Darkness, published
April 1, 1995, on the World Wide Web,
at URL http://wearcam.org/theory_of_darkness.html.
DRAWINGS
The invention will now be described in more detail, by way of
examples which in no way are meant to limit the scope of the invention,
but, rather, these examples will serve to illustrate the invention
with reference to the accompanying drawings, in which:
FIG. 1 illustrates a wallet in which an individual may carry his or
her identification, such that his or her papers are in order, within the
wallet, yet designed so that he or she cannot open it himself/herself without
the kind help of an official such as an SS man with proper identification.
FIG. 2 illustrates an alternative of the safety wallet
which requires a valid fingerprint scan of a finger other than the owner's
in order for it to open up and reveal the owner's papers in order.
DETAILED DESCRIPTION OF THE DRAWINGS
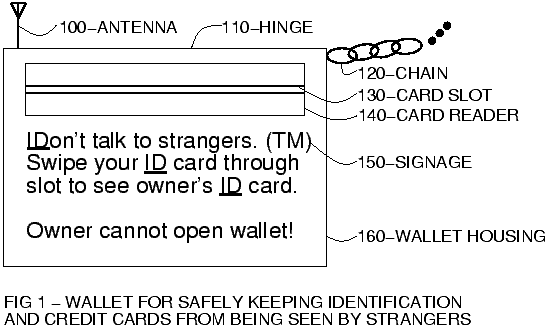
FIG. 1 is a diagram depicting a safety wallet used to keep
passports, identification, or other papers in order, as might be
required by organizations that like to screen for or keep out undesirables.
An antenna 100 keeps the wallet on the Internet or the like, and a hinge
110 allows it to open up but only after an identification of the person
wishing to see the user's papers has occurred over the radio link provided
by antenna 100. A tether (chain, cable, or the like)
120 keeps the wallet attached to the user's body.
Preferably tether 120 is such that it can be threaded around the user's
waist and then fed into the open wallet, such that access to the end
is needed to detach the tether from the user, and access to the end
requires opening the wallet. Alternatively, a special strap around the
waist or ankle may be held in place by a cable similar to those used to
lockdown computers, which then is inserted into the wallet prior to closing it.
Alternatively, the tether may be wireless, such that a person stealing the
wallet will be subdued or marked with chemical means, such as that manufactured
under the trade name Dye Witness (TM). A thief taking the wallet beyond reach
of a corresponding wearable radio transmitter will simply cause the device to
switch into a protective mode of spraying with chemicals.
Similarly, attempts to force open or bypass the lock on the wallet will
result in similar discharge of chemical disincentives.
To open the wallet, an official must slide a government issued ID card through
slot 130 in card reader 140, as indicated by signage 150 upon wallet housing
160. If the ID card is valid, and is found by way of antenna 100 to not
have been reported as stolen, then the locking mechanism
of wallet housing 160 is released so that the official can see that the wallet
owner's papers are in order.
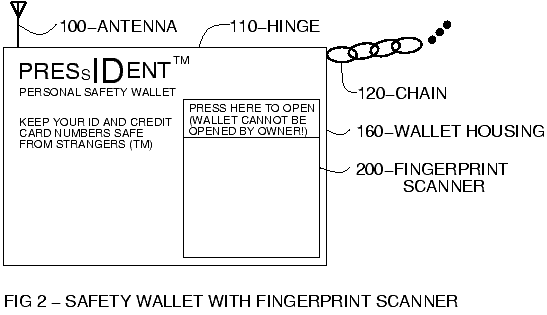
FIG. 2 depicts
a version of the wallet embodiment of the invention that uses a fingerprint
scanner instead of a card reader. The instructions simply direct the official
wishing to see the owner's papers to press on a certain portion of the wallet
to open it.
This portion of the wallet
is really a miniature fingerprint scanner similar to those used in
the BioMouse (TM) computer fingerprint scanner.
The wallet checks to make sure the scanned fingerprint is a valid
fingerprint and is not that of the
owner, prior to releasing the mechanism that allows the wallet to open.
BENEFITS OF THE INVENTION
The apparatus of this invention allows the wearer to
enjoy the benefits that normally only go to building owners.
Benefits include safety, security, and the ability to not
interact with undesirables.
Moreover, just as buildings often have video surveillance systems and
biometrics, the user of the apparatus also has a similar personal safety
device, that keeps a record of interactions between the
user and his/her environment.
In many ways, the apparatus may be thought of as a building built for
one occupant. The apparatus may be of particular benefit to the homeless,
who have no place to call their own, and who are often stopped and asked
for identification by people who do not show them identification.
Steve Mann
April 1, 1999

